

- Navigation
- Main Page
- Community portal
- Current events
- Recent changes
- Random page
- Help
- Toolbox
- Page information
- Permanent link
- Printable version
- Special pages
- Related changes
- What links here
{{#eclipseproject:technology.higgins}}1. To generate a keystore, you need a JDK installed with its /bin directory in your path
2. Create a keystore using this command:
keytool will ask you to enter the values for Common Name (CN), Organizational Unit (OU), Oranization(O), Locality (L), State (S) and Country (C). CN should match the domain name of your webapp if you are planning to use this keystore for your servlet container
You can verify keystore contents using this command:
Copy key from one keystore to another For example you can copy the key pair created in section 'Generate a public/private key pair and a self-signed certificate' with the following keytool command: keytool -importkeystore -srckeystore mystore.jck -destkeystore myotherstore.jks -srcstoretype jceks -deststoretype jks -srcstorepass mystorepass -deststorepass myotherstorepass -srcalias myserverkey. To create a private key and its corresponding public-key certificate using Java tools, you would do something like: $ keytool -genkeypair -keyalg rsa -keysize 2048 -alias jdavies -keystore jdavieskeys.jks -dname 'CN=Joshua Davies' $ keytool -certreq -alias jdavies -keystore jdavieskeys.jks jdaviescert.csr (get the CSR signed by a CA. Tells keytool to generate a public-private key pair.keystore Specifies the path and file name of the keystore to be created (if it does not already exist) or to be added to (if it already exists). A keystore is a file that contains one or more public-private key pairs. Y This option will read a private OpenSSH format file and print an OpenSSH public key to stdout. Specify the private key with the -f option, yours might be dsa instead of rsa. The name of your private key probably contains which you used. The newly generated public key should be the same as the one you generated before. One of the tricks that were required from time to time was extracting the private key and public key (certificate) from Java KeyStores. Extracting the Private Key With OpenSSL and Keytool.
3. Generate the Certificate Signing Request (CSR) using this command:
Submit contents of csr-for-myserver.pem file to your CA for signing
You can get a trial certificate from Thawte at https://www.thawte.com/cgi/server/try.exe
4. Save the signed certificate from CA to a file signed-cert.pem
You can see the contents of the signed certificate using this command:
5. Download Root certificate from CA. You can download Thawte Test Root Certificate from http://www.thawte.com/roots/.
6. Import Root Certificate to keystore using this command:
where root-cert.pem is the Root Certificate from CA
7. Verify contents of keystore using this command:
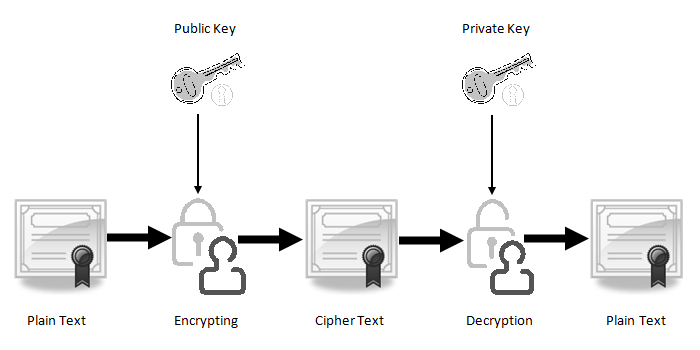
8. Import CA signed certificate to keystore
Keytool Generate Public Private Key Pair
9. Verify contents of keystore using this command:
The most important thing you want to see is that, under the private key alias, additional information is being displayed. You're looking for this:
How to import existing .key and .crt into .jks
Assume you have an existing .key and .crt from your Apache configuration.
You do this:
1. You convert the private key into PKCS#8 format:
2. Since the stupid Java keytool doesn't allow you to import private keys, you download this tool:
3. Now you can import the key into the Java Keystore:
4. Now you have the Java Keystore:
Generate Public Private Key Pair
5. Delete the tmpfile: